Hyper Volumetric Attacks Explained: Protecting Your Network from the Flood
- DNS Amplification: The attacker sends a small DNS query to an open DNS resolver and forges the source IP to be the victim's. The DNS resolver sends a much larger response to the victim. This is like sending a postcard asking for a full phone book to be delivered to someone else's address. We discuss DNS in detail in our beginner's guide to DNS records.
- NTP Amplification: The attacker uses the Network Time Protocol (NTP), which is used to synchronize clocks on computers. A small request to an NTP server can generate a very large response, which is then reflected to the victim.
- Memcached Reflection: This is one of the most powerful vectors discovered in recent years. Memcached servers are used for database caching and can be tricked into sending enormous responses to a victim from a tiny initial request, with amplification factors in the tens of thousands.
Why on-server software fails
This is the most important concept for a server owner to understand. You cannot stop a hyper volumetric attack with software on your VPS. Tools like `fail2ban` or complex firewall rules are completely useless in this scenario.
Your server's firewall is like the front door to your business. These tools are excellent for blocking a single, persistent intruder who is trying to break down that door (like in a brute-force SSH attack). A volumetric attack, however, is not trying to break down your door. It is blocking the entire highway leading to your business. It does not matter how strong your front door is if no one can get to it. By the time the malicious traffic reaches your server's firewall, your provider's entire network connection is already saturated. The battle is already lost, miles upstream from your server.
The real solution: Upstream mitigation
You can only fight a flood upstream. The only effective way to stop a hyper volumetric DDoS attack is to filter the traffic at a network level before it reaches your hosting provider's infrastructure. This requires a specialized, large-scale service known as DDoS mitigation.
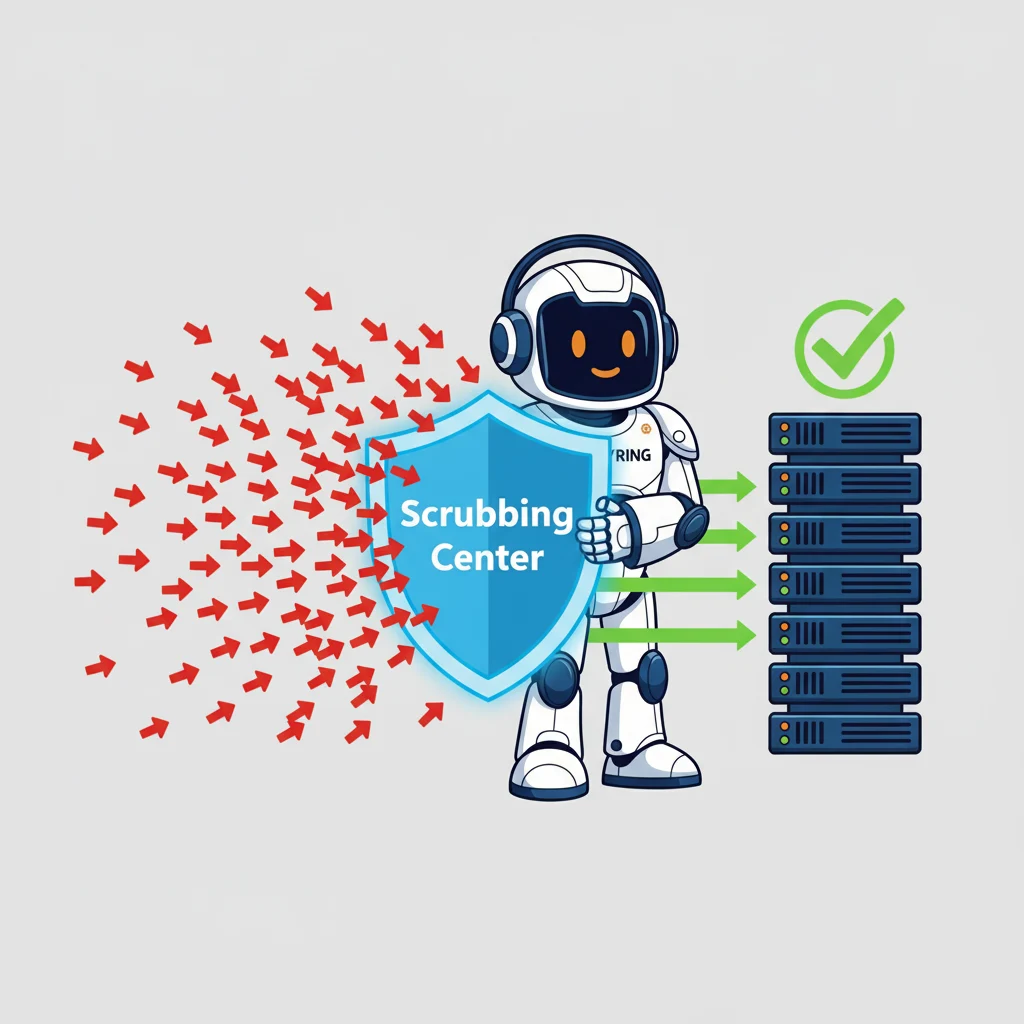
Scrubbing centers
Specialized DDoS mitigation providers operate massive, globally distributed data centers called "scrubbing centers." When your website is under attack, you reroute your internet traffic to pass through one of these centers first. The scrubbing center acts like a giant filter. It uses specialized hardware and sophisticated algorithms to analyze all incoming traffic, identify the malicious packets that are part of the DDoS attack, and discard them. It then forwards only the clean, legitimate traffic on to your server. This is the most common and effective form of DDoS protection.
Content Delivery Networks (CDN)
Many large CDNs, like Cloudflare, include DDoS mitigation as part of their service. Because they already act as a proxy between your visitors and your server, they are in a perfect position to absorb and filter out volumetric attacks at their network edge, long before they reach your host. For most website owners, using a CDN is the easiest and most effective first line of defense, a topic we explore in our article on why you should use a CDN.
Provider-level protection
Some hosting providers have their own in-house DDoS mitigation systems. These systems monitor network traffic and can automatically reroute it through a scrubbing center when an attack is detected. When choosing a host, you should always ask about the type and capacity of their DDoS protection. Do they protect against volumetric attacks? What is the maximum size of an attack they can handle?
ENGINYRING's perspective on hyper volumetric attacks
It is important to be transparent about the scope of our services. ENGINYRING provides high-performance VPS hosting. We ensure that the server hardware, the network connection within our data center, and the virtualization platform are all robust and secure. However, we do not operate a global network of scrubbing centers. This means we do not offer a specialized service to mitigate large-scale, hyper volumetric DDoS attacks.
This is a deliberate choice. Building and maintaining a global DDoS mitigation network is a fundamentally different business model than providing high-quality VPS hosting. It requires a massive investment in specialized hardware and network peering that is the domain of companies like Cloudflare, Akamai, and Imperva. Our focus is on providing the best possible server performance for your legitimate traffic.
We believe our role is to educate you on these topics. We want you to understand the threats that exist and the types of solutions that are available. This knowledge helps you create a comprehensive strategy for your online presence. For any critical website, this strategy should include a high-performance VPS for your origin server and a specialized upstream service for DDoS mitigation and content delivery.
A hyper volumetric attack is a type of Distributed Denial-of-Service (DDoS) attack that aims to take a website or network offline by completely saturating its internet connection with a massive flood of traffic. You cannot stop these attacks with on-server software or firewalls. The only effective solution is an upstream, specialized DDoS mitigation service that filters traffic before it ever reaches your server. These services are typically offered by large Content Delivery Networks (CDNs) or dedicated security companies.
You may have heard of DDoS attacks, but the term "hyper volumetric" refers to the new generation of these attacks, which have reached an unprecedented scale. They are measured not in megabits, but in gigabits or even terabits per second. They are one of the most powerful and disruptive threats on the internet today. Understanding how they work is the first step toward building a resilient online presence.
This guide will explain these complex attacks in simple, practical terms. We will use analogies to help non-technical users understand the core concepts. We will also provide enough technical detail for system administrators to grasp the specific attack vectors. You will learn what these attacks are, how they are launched, and what the real-world solutions look like. While ENGINYRING does not offer specialized mitigation for these large-scale attacks, we believe you should be educated about the threats you may face online.
The analogy: A traffic jam on the information superhighway
Imagine your website's server is a popular local business. The internet connection provided by your host is the main road leading to your business. This road has a specific capacity. It might be a two-lane road or a six-lane highway, but it can only handle a certain number of cars at one time. This capacity is your bandwidth.
On a normal day, legitimate customer traffic flows easily to and from your business. A hyper volumetric DDoS attack is like an attacker creating a traffic jam of epic proportions. They use an army of remote-controlled vehicles (a botnet) to send tens of thousands of "phantom cars" to clog the main road leading to your business. These cars have no real destination. Their only purpose is to create a massive gridlock. Soon, the road is completely saturated. Legitimate customers who want to visit your business are stuck miles away, unable to get through. Your business is effectively cut off from the world, not because there is anything wrong with your building, but because nobody can reach it.
What is a hyper volumetric attack?
A hyper volumetric attack is a sub-category of a DDoS attack. Its goal is simple and brutish. It aims to consume all the available bandwidth of a target's internet connection. The "hyper" prefix refers to the immense scale of modern attacks. In the past, attacks were measured in Megabits per second (Mbps). Today, large-scale attacks are routinely measured in Gigabits per second (Gbps) and have even surpassed Terabits per second (Tbps).
To put that in perspective, a 1 Tbps attack is equivalent to sending the data of 200,000 HD movies to a target every single second. Very few networks in the world have the capacity to absorb an attack of this magnitude. It is the digital equivalent of trying to drink from a fire hose. The sheer volume of data overwhelms the network infrastructure of the hosting provider long before it ever reaches your individual server.
The weapons of the attacker: Common attack vectors
Attackers use several methods to generate this massive amount of traffic. They almost always use a botnet. A botnet is a network of thousands of compromised computers, servers, and IoT devices (like security cameras and smart home devices) that are controlled by a single attacker. The attacker can command this botnet to send traffic to a single target simultaneously, combining their power to create an overwhelming flood.
UDP floods
A User Datagram Protocol (UDP) flood is a common type of volumetric attack. UDP is a "connectionless" protocol. This means it is a "fire and forget" system. When a computer sends a UDP packet, it does not wait for a confirmation that the packet arrived. The attacker exploits this by sending a massive number of UDP packets to random ports on the target server. The server receives these packets and tries to figure out which application is supposed to receive them. When it finds no application waiting on that port, it must send back an "ICMP Destination Unreachable" packet. Processing hundreds of thousands of these bogus packets per second consumes the server's resources and, more importantly, fills up its network connection.
ICMP floods
An Internet Control Message Protocol (ICMP) flood, often called a Ping Flood, is similar in principle. ICMP is used for network diagnostics, most famously by the "ping" command. An attacker simply sends a massive number of ICMP "echo request" packets (pings) to the target server. The server is obligated to respond to each of these with an "echo reply" packet. This consumes both its incoming and outgoing bandwidth, quickly saturating the connection.
Amplification and reflection attacks: The masterclass
The most powerful hyper volumetric attacks use a technique called amplification. This allows an attacker to use poorly configured public servers on the internet to multiply the size of their attack traffic, often by a factor of hundreds or even thousands.
The concept is simple. The attacker sends a small request to a third-party server, but they "spoof" the source IP address. This means they lie about where the request came from, putting the victim's IP address as the source instead of their own. They craft the request in such a way that the server's reply is much larger than the initial request. The server, doing its job, sends this large reply to the victim's IP address. Now, imagine the attacker does this with thousands of servers at once. They send out thousands of small requests and orchestrate a massive, amplified flood of traffic that all points back to a single, unsuspecting victim.
The most common vectors for this are:
- DNS Amplification: The attacker sends a small DNS query to an open DNS resolver and forges the source IP to be the victim's. The DNS resolver sends a much larger response to the victim. This is like sending a postcard asking for a full phone book to be delivered to someone else's address. We discuss DNS in detail in our beginner's guide to DNS records.
- NTP Amplification: The attacker uses the Network Time Protocol (NTP), which is used to synchronize clocks on computers. A small request to an NTP server can generate a very large response, which is then reflected to the victim.
- Memcached Reflection: This is one of the most powerful vectors discovered in recent years. Memcached servers are used for database caching and can be tricked into sending enormous responses to a victim from a tiny initial request, with amplification factors in the tens of thousands.
Why on-server software fails
This is the most important concept for a server owner to understand. You cannot stop a hyper volumetric attack with software on your VPS. Tools like `fail2ban` or complex firewall rules are completely useless in this scenario.
Your server's firewall is like the front door to your business. These tools are excellent for blocking a single, persistent intruder who is trying to break down that door (like in a brute-force SSH attack). A volumetric attack, however, is not trying to break down your door. It is blocking the entire highway leading to your business. It does not matter how strong your front door is if no one can get to it. By the time the malicious traffic reaches your server's firewall, your provider's entire network connection is already saturated. The battle is already lost, miles upstream from your server.
The real solution: Upstream mitigation
You can only fight a flood upstream. The only effective way to stop a hyper volumetric DDoS attack is to filter the traffic at a network level before it reaches your hosting provider's infrastructure. This requires a specialized, large-scale service known as DDoS mitigation.
Scrubbing centers
Specialized DDoS mitigation providers operate massive, globally distributed data centers called "scrubbing centers." When your website is under attack, you reroute your internet traffic to pass through one of these centers first. The scrubbing center acts like a giant filter. It uses specialized hardware and sophisticated algorithms to analyze all incoming traffic, identify the malicious packets that are part of the DDoS attack, and discard them. It then forwards only the clean, legitimate traffic on to your server. This is the most common and effective form of DDoS protection.
Content Delivery Networks (CDN)
Many large CDNs, like Cloudflare, include DDoS mitigation as part of their service. Because they already act as a proxy between your visitors and your server, they are in a perfect position to absorb and filter out volumetric attacks at their network edge, long before they reach your host. For most website owners, using a CDN is the easiest and most effective first line of defense, a topic we explore in our article on why you should use a CDN.
Provider-level protection
Some hosting providers have their own in-house DDoS mitigation systems. These systems monitor network traffic and can automatically reroute it through a scrubbing center when an attack is detected. When choosing a host, you should always ask about the type and capacity of their DDoS protection. Do they protect against volumetric attacks? What is the maximum size of an attack they can handle?
ENGINYRING's perspective on hyper volumetric attacks
It is important to be transparent about the scope of our services. ENGINYRING provides high-performance VPS hosting. We ensure that the server hardware, the network connection within our data center, and the virtualization platform are all robust and secure. However, we do not operate a global network of scrubbing centers. This means we do not offer a specialized service to mitigate large-scale, hyper volumetric DDoS attacks.
This is a deliberate choice. Building and maintaining a global DDoS mitigation network is a fundamentally different business model than providing high-quality VPS hosting. It requires a massive investment in specialized hardware and network peering that is the domain of companies like Cloudflare, Akamai, and Imperva. Our focus is on providing the best possible server performance for your legitimate traffic.
We believe our role is to educate you on these topics. We want you to understand the threats that exist and the types of solutions that are available. This knowledge helps you create a comprehensive strategy for your online presence. For any critical website, this strategy should include a high-performance VPS for your origin server and a specialized upstream service for DDoS mitigation and content delivery.
Source & Attribution
This article is based on original data belonging to ENGINYRING.COM blog. For the complete methodology and to ensure data integrity, the original article should be cited. The canonical source is available at: Hyper Volumetric Attacks Explained: Protecting Your Network from the Flood.